We compiled a short list of business technology terms that are useful to keep on hand when looking for software solutions for your business or when speaking with an IT Service Provider. Because, sometimes a short and simple definition is all you need, and that’s exactly what we have here.
‘BUSINESS CONTINUITY’ Terms
| Business Continuity: | Set of activities to ensure an organization can respond to a crisis or disaster in a timely manner in order to continue business operations as usual |
| Business Continuity Solution: | A software solution implemented at an organization to ensure continuous, secure data backup as well as quick restoration of data (to its former state) if a disaster or crisis strikes |
| Disaster/Crisis: | Any event that has the power to disrupt an organization’s activities |
| Downtime: | A period of time that a company’s system is unavailable (or has failed to perform its normal functions) |
| Data Backup: | The process of taking a secure copy of a person or company’s data files and storing it on an external medium or device for future use in case of disaster |
| Off-site Backup: | The backing up and storing of data to a place a distance away from a company’s physical location |
| VM: | Virtual Machine; an imitation of a physical computer; basically, a VM allows you to run other operating systems within your current OS
Virtualization = The creation of a virtual version of an operating system, network, server, storage, device, etc. |
| Restoration: | The process of returning a company to its normal operations by repairing hardware & recovering data from the business’ backup methods;
File Restore = recovery of specific files] [Bare Metal Restore = restoration of complete VM from “bare metal” (without previously installed software or OS)] |
| RTO: | Recovery Time Objective; a parameter in disaster recovery used to calculate the duration of time within which a business must be restored back to normal before the disruption seriously impedes business operations |
| RPO: | Recovery Point Objective; a parameter in disaster recovery used to calculate the point in time that can pass during a disruption before the quantity of data lost during that period is greater than the company’s max allowable threshold |
‘CLOUD’ Terms
| Cloud Computing: | A means of storing & processing a company’s data. Rather than housing the data on a customer’s servers (on-site), it is housed in a network of servers in a secure Data Centre; therefore the data is accessed remotely (over the Internet)
|
| Public Cloud: | Multi-tenant environment; this form of cloud computing relies entirely on a Service Provider; all services (servers, data storage and applications) are delivered via the Internet |
| Private Cloud: | Single-tenant environment or “cloud computing at home”; it is a cloud computing platform that is implemented within the company’s firewall, giving them greater control over the data and its security; has same features as a public cloud |
| Hybrid Cloud: | An integrated cloud service (combination of private and public clouds) where some applications or resources are provided and managed on-premises and others externally (in a public cloud) |
| On-Premise: | Traditional way of delivering IT services; when a company chooses to have their own server room to host all their IT equipment, that is typically managed by their own in-house IT staff (can also be managed by an outsourced IT team) |
| Off-Premise: | (Or off-premise hosting environment); delivering IT services off-site, where IT services are managed by a Third Party Provider and servers and hardware is leased by this provider |
| Data Centre: | A secure facility that houses servers and telecommunications equipment. When speaking about “cloud hosting”, these Data Centers are the homes of these cloud services |
| SaaS: | Software as a Service; This is a software distribution model where an application is provided to a customer on a subscription basis, as the software is hosted by the Service Provider and is not owned by the customer. Typically, the software application is provided over a network (Internet) |
| Managed Hosting: | When a Service Provider leases servers and required associated hardware to a customer. It is monitored and maintained by the Service Provider and all hardware is at the provider’s facility |
| Application Hosting: | When a business moves their software to an off-premise hosting environment (usually to the cloud) |
If you have any terms you’d like us to add to the list, simply leave us a comment in the section below!
Founded in 1994 in the United States, Amazon.com is the world’s largest online retailer of books, apparel, electronics, music and many other products. Today, it has become one of the world’s leading e-commerce platforms. Amazon keeps pace with technology, using it to minimize the human error factor and improve efficiency. Amazon was an early adopter of process automation and electronic data interchange for its e-commerce platform.
Read more: Free Guide – Introduction to EDI Communication
Amazon Vendor Central or Amazon Seller Central?
We’ve heard these terms so often:“Amazon Vendor Central” and“Amazon Seller Central”. So, what are these terms? what do they mean? Let’s explore both, one at a time. Any company wishing to sell its products or services on the Amazon platform will be configured on this platform either in the “Amazon Vendor Central” portal or in the “Amazon Seller Central” portal. What’s the difference?
Amazon Vendor Central
Firstly, Vendor Central is a web portal used primarily by manufacturers and distributors. Access to Vendor Central is by invitation only.
A company that sells its products/services directly to Amazon, which in turn sells them to the end consumer, will be configured on Amazon’s Vendor Central portal. In a similar case, Amazon is the buyer of the company’s products. Amazon will sell the products under its own brand name to the end consumer. Usually, when a package is shipped from Amazon to the end consumer, packages are marked as follows: “Ships from and sold by Amazon.”
Companies using Amazon Vendor Central are considered 1P (or first seller).
Amazon Seller Central
Once again, Seller Central is a Web portal used primarily by the seller (or store owner on Amazon). Amazon offers its e-commerce platform for businesses that want to run their own stores on its platform and give them the opportunity of the Amazon marketplace. This service is offered against a fixed monthly fee for use, and other fees for transactions.
In this case, the manufacturer or distributor will sell its own products directly to consumers on the Amazon marketplace using the Seller Central account.
As a seller on the market, a subscriber will be able to manage the execution and logistics of his seller account according to (2) different options:
- Fulfillment by Merchant (FBM): The seller can manage shipping, customer service and returns for each individual order. A ” Fulfillment by Merchant” order will be shipped from the merchant’s warehouse. The seller may also use the drop-shipping method subject to compliance with the Amazon Drop Shipping Policy.
- Fulfilled by Amazon program. (FBA): Sellers will be able to allow Amazon to manage the fulfillment of their orders, via inventory sent to Amazon warehouses. Obviously, the seller has to list its products on Amazon as part of the FBA program, and Amazon will have additional charges for the use of its fulfillment resources.
Amazon data integration
Integration with Amazon, is the process of implementing one or more feeds to extract relevant data from the company’s system and send it to its Amazon account/store (i.e. product and pricing information, inventory data …). At the same time, extract order, customer and payment information from the Amazon account/store and send it to a company’s internal software system.
Automating data integration with Amazon
As described above, integration with Amazon is very important and crucial to a successful e-commerce business. The integration process doesn’t happen just once. It’s a continuous process of keeping the “synchronization” as close to “real time” as possible.
To be able to maintain a permanent, seamless integration between a company’s Amazon account and its internal software system, companies have no choice but to adopt “automated integration”.
Benefits of integration with Amazon
Here are the 5 main advantages of integrating with Amazon, which will also be detailed in another article in the future:
- Ability to deliver your products quickly to your customers in a highly competitive market
- Avoid chargebacks, credits and penalties related to poor or non-existent inventory and stock status on your Amazon account
- Avoid unnecessary non-productive human errors when manually handling orders received from your Amazon account
- Gain visibility and credibility for your Amazon account and products.
- Comply with Amazon’s terms and conditions for product delivery.
Amazon options for efficient integration?
Amazon offers (2) integration methods depending on the type of account configured for your company:
- EDI (X12) integration (in North America) for Vendor Central account customers
- Amazon Marketplace Web Service (Amazon MWS) for Seller Central account customers
Messages to exchange with Amazon
Whether you use EDI X12 or Amazon MWS to exchange messages, the following documents are mandatory for successful integration:
Amazon works with various suppliers and types of EDI software:
EDI X12 documents
- EDI 846 – Inventory status
- EDI 810 – Invoice
- EDI 850 – Purchase order message (Customer triggered)
- EDI 855 – Order acknowledgement
- EDI 856 – ASN (advance shipping notice)
- EDI 860 – Order change notification
Amazon MWS messages
- Products
- Controls
- Acknowledgement of order
- Order payment
Why integration with Amazon is crucial
Integration with Amazon is crucial for several reasons:
- Huge customer base: Amazon is the world’s largest e-commerce platform, with millions of active customers. By integrating your company or product with Amazon’s platform, you can access this vast customer base and considerably increase your visibility and sales chances.
- Logistics infrastructure: Amazon has a well-established logistics infrastructure and network of warehouses around the world. By integrating your business with Amazon, you can benefit from this infrastructure for storing, packing and shipping your products. This saves you time and resources by outsourcing these activities to Amazon.
- Consumer confidence: Amazon is known for its high-quality customer service and solid purchase guarantees. By being integrated with Amazon, you benefit from the reputation and trust associated with the Amazon brand, which can reassure consumers and encourage them to buy your products.

- Marketing and promotional tools: Amazon offers various marketing and promotional tools for sellers integrated into its platform. You can take advantage of targeted advertising, personalized recommendations, loyalty programs, and other marketing strategies to reach a wider audience and increase your sales.
- Process simplification: Integrating your business with Amazon enables you to simplify certain business processes. For example, you can use Amazon’s features to manage orders, stock tracking, payments, and returns. This allows you to concentrate your efforts on other aspects of your business, such as product development or range expansion.
Amazon integration for your business
Don’t miss out on the huge opportunity for your company to sell on Amazon. We provide integration and automation for Amazon Seller Central users as well as EDI integration for Vendor Central users. Contact us today for more information, to request a quote, or schedule a demonstration.
Integration platform for business efficiency
Information technology is developing rapidly. Many experts call IT the fastest-growing sphere of human activity. Systems and applications integration plays an important role in the IT space, and has a significant impact on company performance as well as on all industrial and commercial sectors. That’s why we’ve seen a surge in corporate interest when it comes to integration…
What is “systems integration”?
According to Wikipedia: system integration is defined in engineering as the process of bringing together subsystem components within a single system (an aggregation of cooperating subsystems so that the system can provide overall functionality).
But it would be a mistake to think of “systems integration” as simply the assembly of hardware and software tools; the essence of the concept is much broader than that.
“Systems integration” is an activity aimed at improving a company’s efficiency, decision-making and information quality through an automated process, where “heterogeneous” systems can communicate and integrate with each other in real time.
Most companies in today’s business environment run many “heterogeneous” systems and software, yet there is no established communication between them. This type of environment creates a lot of inefficiencies and poor quality information, which in most cases leads to reduced profits and delays in management decisions.
Automated system integration acts as a bridge where data flows between heterogeneous systems, software applications and databases in multiple directions, based on predefined business rules, as if the systems were totally “homogeneous”.
Why do companies need “systems integration”?
Increasingly, companies are arming themselves with software and hardware to solve specific business needs. All this while adding new modules and “stand-alone” systems to their IT management system. Most of the time, these solutions don’t communicate natively with each other.
While the adoption of a specific software application (cloud or on-premise) may meet a company’s business requirements and solve a business problem, it will create a series of new challenges in its own right:
- Redundant data entry; most of the data already exists in another system.
- Need to hire more staff to manage more systems
- Open the door to more human error when managing new systems.
The above challenges are relevant to companies of all sizes, whether small, medium or large.
How to solve integration problems?
To solve the integration problems identified in the previous point, companies should not hesitate to adopt integration projects to synchronize and orchestrate IT software, databases, processes and equipment.
To achieve this, companies will need to adopt an “integration platform” capable of exhibiting the following properties:
- Easy to use (drag and drop)
- No coding required
- Quick to learn, develop and deploy
- Easy debugging and simple error handling
- Several options for triggering and launching processes and flows
- Able to connect to most of the databases commonly used in today’s market
- Able to connect to brand-name software systems (e.g. SAP, Salesforce, Oracle, SugarCRM …) with connectors certified by the manufacturer.
- Generic API-based connectors for IoT projects
- Extensible to go beyond “out-of-the-box” where you can build your own connectors for specific solutions.
Benefits of systems integration
The benefits of implementing a robust API-based integration that can connect to a wide range of enterprise ecosystems are invaluable. Here are the 5 advantages:
- Real-time data synchronization
Having a robust integration platform responsible for orchestrating and synchronizing data and processes, eliminates delays in data publication. Data is synchronized between different systems in real time, without the need for human intervention.
- Faster data processing
With an automated integration platform, which is able to synchronize data and trigger flows and processes efficiently based on rules and conditions, data processing also becomes real-time, eliminating the need for data extraction, transformation and loading (ETL). No need for a separate ETL tool.
- Improved employee productivity
Data synchronization and orchestration obviously eliminate a lot of time and effort for employees to manage and enter/extract data from one system to another. Employees can focus on business-related problems business-related issues, where they can generate more revenue, rather than entering and manipulating data in “heterogeneous” systems.
- Faster decision-making
Having a robust integration platform, with all the benefits identified above, business leaders will be able to make quick decisions and avoid the time-consuming process of extracting data from different systems and merging the sets to obtain a unified data sheet.
- Increased profitability
Taken together, the above benefits will significantly increase the profitability of any company with heterogeneous IT systems and applications.
 What are the signs that a company needs an integration platform?
What are the signs that a company needs an integration platform?
Here are the main signs in any company that an integration platform is needed to improve business processes.
- Your company has several stand-alone software systems, with no direct links between them.
- Your company has a combination of on-premise and cloud-based software solutions that are not connected.
- Employees spend a lot of time on their daily work, feeding several systems
- Your company has an e-commerce site managed separately from the internal ERP system
- The company’s IT department is unable to provide reports and analyses on time.
- Unable to meet your customers’ business requirements, deliver within 48 hours
- There are major data mismatches between systems and solutions, due to redundancy.
- Many employees work on report writing and data entry work
- No visibility of company equipment data and performance (production machines, cameras, field service data, etc.).
Are you looking for an integration platform solution for your company?
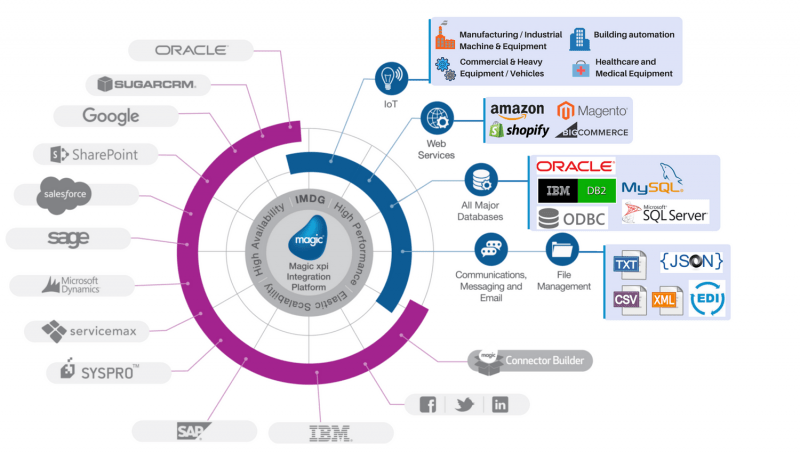
For over 18 years, our company has been an official partner of Magic Software Enterprises, a global provider of software solutions, supplying Magic xpi, an integration platform based on a fully reliable SOA, and API-driven for all necessary connections.
The Magic xpi business integration platform provides enterprise-level integration, business process automation and data synchronization, with complete security and proven reliability.
Implementing a wide range of certified and optimized connectors and adapters, Magic xpi integrates leading ERP, CRM, financial and other enterprise systems, such as SAP, Oracle, Salesforce, Microsoft, IBM, Google, and many more.
Are you looking for integration solutions? Contact us today
Ransomware: Why You Should Care
Viruses extortionists (ransomware, cryptoviruses) work in a similar way: they block the user’s desktop, encrypt important documents and files saved on the computer, then delete the originals and demand a ransom. Typically in Bitcoin, so they can provide you with a key to unlock your computer and to be able to continue working and have access to your saved files. Often the creators of cryptoviruses have strict conditions for the terms of payment of the redemption. If the owner of the files does not fit within these terms, the key is deleted and it will be impossible for the user to restore the files.
Ransomware is the most massive and significant attacks of computer viruses in the world.
Here a chronology of the first viruses in history, as well as the largest-scale virus computer attacks.
In 1971, the first program in the world, which was able to independently reproduce copies of itself on a computer network, was created by the engineer of the American technology company BBN Technologies, Bob Thomas. The program, called Creeper was not malicious: its functionality was limited to self-copying and displaying the message: “I’m the creeper, catch me if you can!” A year later another BBN engineer, e-mail inventor Ray Tomlinson, created the first anti-virus that self-replicated on the network computers and deleted Creeper.
The first virus created in 1981 caused an uncontrolled “epidemic.” This virus spread using a technique now known as a boot sector virus. A virus called Elk Cloner was created by a 15-year-old American high school student Richard Skrenta by infecting the Apple II operating system. The virus infected the magnetic diskettes and, after the 50th access to the infected media a blank screen appears and a joke poem message was displayed. In some cases, the virus could also damage the floppy disk.
The first malicious program Michelangelo that infected over 1 million computers worldwide appeared in 1991 in Australia was written for IBM-compatible personal computers (PCs) and the DOS operating system. Other information from the disk could be restored, but it was difficult for an ordinary PC user to do it. The creator of the virus remained unknown, some cases of program activation were recorded until 1997.
On June 2, 1997, Chen Ing-hau, a student at the University of Datong (Taipei, Taiwan), created the first version of the Chernobyl virus (“Chernobyl” or CIH – according to the first syllables of the author’s name). The virus infected computers with operating systems Windows 95 and 98, triggers on April 26 of each year, the anniversary of the Chernobyl nuclear disaster. The virus erased the boot sector of the hard disk and, sometimes, the BIOS data – the boot sector of the computer. In the latter case, it was required to change the chip on the motherboard or even acquire a new computer, since the old one was out of order.
It is estimated that more than 60 million PCs were infected worldwide, and the damage exceeded $ 1 billion.
On May 5, 2000, the world’s largest epidemic of computer virus began. Created by Filipino students Reonel Ramones and Onel De Guzman, the “worm” ILOVEYOU sent itself to all e-mail contacts of the owner of the infected PC and replaced most of the files with documents, images and music on copies of itself. Only in the first 10 days of the epidemic, the number of infected computers exceeded 50 million. To protect themselves from the epidemic, many government agencies around the world have temporarily disconnected e-mail. The total damage was subsequently estimated at $ 15 billion. The Philippine police quickly found the creators of the virus. However, they went unpunished due to the lack of an article in the local criminal code providing responsibility for computer crimes.
On September 2010, the Stuxnet virus hit the computers of employees of the nuclear power station in Bushehr (Iran). It created problems in the functioning of centrifuges of the Uranium Enrichment Complex in Natanz. According to experts, Stuxnet was the first virus to be used as a cyber weapon.

On May 12, 2017 a significant number of computers with Windows as operating system were attacked by a virus-extortionist WannaCry. The virus encrypts user files so that they cannot be used. For decrypting the data, the attackers demanded $ 600 in the crypto currency of bitcoin.
According to Europol, the attack affected more than 200,000 computers across 150 countries. The four most affected countries were Russia, Ukraine, India and Taiwan according to Kaspersky Lab. The attack, in particular, affected the National Health Service hospitals of Great Britain. Up to 70,000 devices including computers, MRI scanners, blood-storage refrigerators, and theater equipment have been affected. Cyber risk modeling firm Cyence estimates the potential costs from the hack at $4 billion.
Don’t Miss: The Dangers of Ransomware & How To Overcome A Cyber Attack
On June 27, 2017, from the attack of a new variant of Petya Ransomware many of large organizations have suffered in multiple countries, but especially in Ukraine and Russia.
The Petya virus spreads through links in e-mail messages and blocks the user’s access to the computer hard drive, demanding a ransom of $ 300 in bitcoins. This is similar to the malicious program WannaCry. During this attack, the radiation monitoring system at Ukraine’s Chernobyl Nuclear Power Plant went offline. Some Ukrainian ministries, banks and metro systems were also affected. It is said to be the most destructive cyberattack ever.
The Business Continuity Solution to Ransomware
The best solution to protect your data and company from a different type of cyberattack is QBR (Quick Backup Recovery) Business Continuity Service, powered by Datto and provided by Namtek Consulting Services. QBR entails on-site real-time data and machine backup through virtualization as well as off-site backup to the cloud. This hybrid solution allows for quick recovery during a disaster with no downtime or data loss. For more information about the latest solutions in Backup and Recovery visit us at: Quick-Backup-Recovery.com
Role of EDI Integration in The Global E-commerce Trends 2023
This post was updated to reflect current trends and information.
We get a lot of questions about the relationship between our EDI Services and e-commerce; So, we have decided to close this year by predicting the global e-commerce trends for 2023, and the role of EDI Integration in e-commerce. In this article, you will learn how our popular EDI2XML Fully Managed Services can help increase your e-commerce success in 2023.
The Global E-commerce Trends 2023
2023 is around the corner it’s time to plan your actions. E-commerce continues to show rapid growth, but competition is growing faster than the market itself. This means that it will be not so easy to “win hearts” of buyers, and you can lose them more easily. Customers will be more and more capricious about delivering goods and prices.
2023 will be the year when competition in e-commerce will reach a new level. More and more young companies are appearing in the online marketplace. The big, strong brands are heavily promoting their online offerings on the Internet. They are looking to occupy a significant part of the e-commerce market, because consumers are increasingly going online.
According to Statista in 2022, e-retail sales surpassed 5.7 billion U.S. dollars worldwide.
E-commerce in the United States of America
Since the dawn of e-commerce, the main driver for the growth of this market was the United States. Online trading has become a global phenomenon, but the US remained one of the most important markets for e-commerce.
The annual increase in sales via the Internet has led to an explosive growth in e-commerce in the United States over the past 15 years.
According to Digital Commerce 360 US eCommerce grows 7.3% in Q2 2022
Although growth rates remain active, the US market is not so far from saturation point. We can expect that sales to stop growing at such a rapid pace.
The American e-commerce market gave way to China
The situation in the Asian markets is directly opposed, especially in China. According to forecasts, the rapid growth of e-commerce will continue in China. The growth of Chinese online sales is taking a huge share of the global e-commerce market.
Despite the large volume of sales in America, the world record set by the Chinese online giant Alibaba that records $56bn in first post-virus Singles’ Day sales, beating 2019 high.
According to John Caplan, head of North American B2B, Alibaba Group, More than 150,000 brands and merchants doing business on Alibaba’s online platforms.
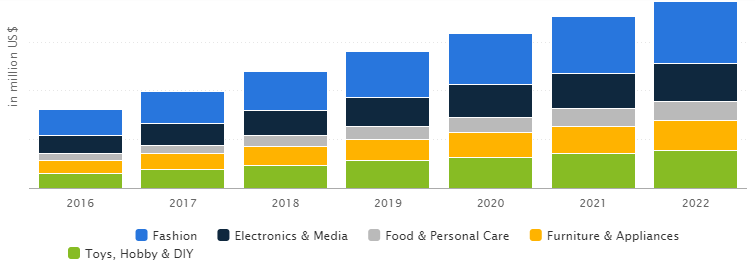
Revenue is expected to show an annual growth rate of 13.9 % resulting in a market volume of US$956,488 m in 2022.
Source: Statista
The growth of e-commerce in Asian countries has serious consequences for companies engaged in online business. To benefit from the new trend, they need to enter the international market with their proposals.
EDI – unlimited possibilities to sell across the globe
The advantage of online trading is that you do not need a physical store in order to start selling in a new country. International delivery of goods is becoming more and more accessible.
Read: Must-Have BigCommerce Integrations
However, you should always keep in mind that it is practically impossible to carry out online business, without full integration of systems between your eCommerce platform and your vendors, including Electronic data interchange (EDI); especially we are now in the international trade and transactions are becoming very “time-sensitive”.
EDI and systems Integration, play a major role in e-commerce. To be a supplier of companies such as Amazon, Wal-Mart, Cabela’s, Bed Bath & Beyond, Costco, and other important retailers, you need to be able to send and receive documents electronically.
EDI has proved its reliability and importance for businesses. Processing orders in digital format automatically increase the speed, accuracy and efficiency of any business.
Fully Managed EDI Service for E-commerce
EDI2XML Managed Services is the perfect option for businesses looking to simplify their entire EDI and integration process with their Trading Partners. This service is ideal for businesses of all sizes, from various industries.
EDI2XML is a full-service offering. Our team of EDI and IT integration experts handle a company’s entire EDI project from start to end. All conversions of EDI files are done at our end, leaving customers with no on-site installation of software or hardware. Their EDI project is on time and within budget.
Keep learning about EDI integration and the MANY benefits it has for your online business by visiting our website EDI2XML.com or contacting us directly today!
RELATED POSTS:
Request EDI2XML Service Pricing Package
Must-Have BigCommerce Integrations
Fully managed EDI service VS HTTP Web Service: Which is Better for Your Business ?
Business Continuity
After consulting with many business owners, I realized that when software experts mention the words “business disaster” or “disaster recovery”, many people are thinking of natural phenomena, or weather events, such as floods, hurricanes, fires, ice storms, earthquakes, tsunamis, windstorms, and so on. Of course these disasters can affect a business, and they can have devastating repercussions, such as extended downtime, property damage, even loss of revenue and more. The probability, however, of such meteorological events is much lower than that of man-made technological events.

Technological and human disasters, including equipment failures, software malfunctions, user errors, security breaches, etc., can also have devastating effects on a company’s operations, resulting in downtime, lost data, lost productivity, lost expenses and more. One hour of downtime can cost companies thousands of dollars for small businesses and hundreds of thousands of dollars for large companies! It is essential to know your maximum downtime (RTO Recovery Time Objective) for your company. How long can you stop and survive? If your RTO is in seconds or minutes, it’s best to make sure you have a business continuity solution with off-site data storage.
Many companies, without a Business Continuity and a disaster recovery plan, many companies fail to recover from disasters. So, before you think to yourself, “we have great weather here or we almost never have power outages, why should I pay for a Business Continuity ?” – remember that your business is more likely to fall victim to ransomware, have an employee accidentally delete an important file or deal with a failing server. No matter how sudden and disastrous the event, you want to be protected. Ask yourself: is my company’s data worth the risk? You may have made it through the last 10 years without a disaster, but can you really guarantee that the next 10 will also be crisis-free? Your employees are human, they can make mistakes.
Ransomware attackers don’t care who you are or how big your company is, they attack everyone. We can never be too sure when a server will fail. There are no certainties, which is why it’s important to have a disaster recovery plan and a Business Continuity Service to guarantee TOTAL data protection, so you can get up and running quickly and easily. It’s not worth risking your company’s reputation and operations.
In our previous blog , we mentioned the term “data assurance”. This is how our customers see their Business Continuity Solution and service. They see it as an insurance policy in place to protect their company’s most important asset – their data! Companies are increasingly willing to pay a monthly fee for Business Continuity Services to ensure that their data is 100% protected and easily recoverable.
There’s no point in simply backing up your data only to find that after a disaster it takes DAYS to recover everything! Now that companies are using comprehensive management systems rather than keeping important information on paper, they are realizing the need for such a backup solution. They are also relying less on those outdated and obsolete tapes and drives to back up their data, and more on hybrid cloud backup.
Lately, we’ve been hearing a lot about “Ransomware”. This type of security breach is currently a big problem for companies, and even individuals, all over the world. The probability of a company suffering a ransomware attack is very high.
In 2016, the US and Canada jointly issued an alert, warning businesses and individuals of “the recent increase in extortion attacks that infect computers with viruses known as ransomware.” This virus not only encrypts a company’s data, but also demands payment to unlock it (Reuters, 2016).
The alert informed people that some of the consequences of ransomware attacks include “loss of information, disruption of current operations, expenses to restore access to company systems and damage to corporate reputation”. Governments have also discouraged victims from paying the pirates, since paying the ransom does not guarantee the release of their files. All it guarantees is that the pirate receives the money and, in some cases, their bank details. (Reuters, 2016)
Ransomware continues to dominate in 2017, with small and larger companies still paying millions of dollars to unlock their encrypted.
There are many ways in which a company can fall victim to a cyber attack. The most common are when computer users click on the wrong link or download an encrypted attachment. Other adulterations include spinning, baiting and heeling.
It’s important to understand why total data protection is essential in today’s business world. Businesses are now run and managed with software systems, so it’s important to ensure that there are no service interruptions in the event of the unexpected. Companies need to protect themselves not only against natural disasters, but also against man-made technological events, which are far more likely to occur.
Reduce your risks with a Business Continuity solution and a solid disaster recovery plan. Contact us today!
YOUR FILES ARE ENCRYPTED! To decrypt your files you need to obtain the private key. To obtain the private key, you need to pay 300 USD.
Any attempt to remove or damage this software will lead to the immediate destruction of the private key by server.
 This message is one that no business owner wants to see pop up on their office computer screen. Ransomware – a nasty and costly virus (or malware) that locks down computers and encrypts data until money (or a ransom) is sent – is not going anywhere. In fact, it seems to be such an epidemic these days as there are new malwares popping up and more victims paying up, which includes individuals, small and large organizations, hospitals, universities, government agencies and more.
This message is one that no business owner wants to see pop up on their office computer screen. Ransomware – a nasty and costly virus (or malware) that locks down computers and encrypts data until money (or a ransom) is sent – is not going anywhere. In fact, it seems to be such an epidemic these days as there are new malwares popping up and more victims paying up, which includes individuals, small and large organizations, hospitals, universities, government agencies and more.
Our team of IT experts has already seen and helped businesses recover from ransomware and other malware attacks and in fact, we’ve recently been hit as well. What has saved us and our customers from incurring high and sometimes damaging costs is the fact that we were all well prepared for such an incident. (Read our previous blog called “Ransomware Detected”)
How? Let me further explain about the costs that businesses can incur from ransomware and what to do to recover easily and quickly from this cyberattack.
First and foremost, it’s important to know that anyone can get hit by ransomware. It is not only large, successful organizations or government agencies. It can be small businesses or individuals. Secondly, it’s criticial that business owners get rid of the thought that “it won’t happen to me or my business – ransomware has been around for years and I’ve never had an incident like that”. This is such a dangerous thought. It may never have happened before but it doesn’t mean that it can’t happen in the future. Cyber criminals are only getting smarter and more powerful. Ransomware has become a billion dollar industry, where about 4,000 cyberattacks are launched every single day (Globe and Mail, May 2017)
Unfortunately, even if managers or IT departments do their best to educate their employees on malware and how to identify suspicious emails, links or attachments, we should never take the chance that one bad email won’t slip through. Ransomware can halt business operations immediately and this is very dangerous. Over the last couple of years, on average, ransomware has cost small businesses over $100,000 per attack due to downtime (some companies have been hit more than once in the span of a few months!!). Most people think that the ransom ($) is the biggest cost that comes from a ransomware attack. However, there are a lot more damages that can be incurred, such as;
- Loss of revenue due to downtime
- Lost customers and damaged reputation
- Loss of productivity
- The cost of hiring IT experts to restore your systems in the days following an attack
- Data loss (!!)
So, even if the ransom is paid rather quickly, it could still take up to a week or more to remove the infection from your systems and get back up and running. (Do you know how much money your company will lose if you are down for a week?) One law firm in the U.S. suffered 3 months of downtime while their systems remained locked! Most smaller companies would not survive this. On top of all of this, companies may never be able to retrieve some of their sensitive business data.
Therefore, the downtime and data loss that companies suffer are two of the biggest threats to a company if attacked by ransomware or any malware. What’s also important to note is that even though the original ransom may be a measly $300 USD, cyber criminals have no morals and can increase this amount at any time and for any reason. For example, hospitals and universities hold highly sensitive information. Cybercriminals are aware that they would pay anything to retrieve their data. Their ransoms are known to be in the thousands – some stories have reported ransoms of $20,000. What’s worse is that if they see how quickly a company pays up the first time they get hit, if they get hit a second time the amount will increase exponentially. It’s a dangerous game and it’s not one any business owner would want to play.
What’s worse, is that most recently, the FBI has urged companies NOT to pay the ransom if their computers get infected. “Paying a ransom doesn’t guarantee an organization that it will get its data back – we’ve seen cases where organizations never got a decryption key after having paid the ransom”, said FBI Cyber Division Assistant Director James Trainor.” (CNN, July 2017)
The Business Continuity Solution to Ransomware
The BEST way to protect your data and company from this type of attack is to implement a Business Continuity and Disaster Recovery plan and software solution, like QBR, paired with educating your employees. They need to know what to look out for; how to identify suspicious emails, attachments and links and once identified to report them to their IT team right away. If anything should occur, the IT team will have a plan of action ready and will deploy a bare metal restore to remove all traces of the virus and go back in time. Depending on how often you chose to backup your data, all that may be lost is an hour or so of data. After that, everything can be back to normal and operations can continue as if nothing ever happened.
Therefore, implementing a Business Continuity solution like QBR truly is a small price to pay to ensure that your data is safe and your company can survive a Ransomware attack, without incurring downtime. Our customers view this service as their insurance policy instead of an added cost to their business. They would rather pay a monthly service to protect their data than take the risk of getting hit by a malware and having to incur major damages.
 It’s not uncommon to find large and small companies either using multiple separate systems or using Excel Spreadsheets and emails to run the business. Most likely, what you’ll find at these companies are employees relying heavily on their emails to track and manage important files and information, miscommunication between departments, inaccurate and outdated data being shared, and more inefficiencies.
It’s not uncommon to find large and small companies either using multiple separate systems or using Excel Spreadsheets and emails to run the business. Most likely, what you’ll find at these companies are employees relying heavily on their emails to track and manage important files and information, miscommunication between departments, inaccurate and outdated data being shared, and more inefficiencies.
As per our previous blog on the “Dangers of Running a Business solely on Microsoft Office tools”, companies are likely to experience the following if they rely heavily on Excel spreadsheets and other Microsoft Office tools;
- Data loss and corruption; Spreadsheets are known to become unstable the more information is added to them.
- Typos and other errors; Sometimes, small typo errors can be difficult to catch but in the long run can cause major problems and headaches.
- In most cases, these spreadsheets are being shared between various departments. What can happen is that various versions of the same file can be passed around and saved by each department. At this time, different information is travelling from person to person, which can also cause serious problems in the future.
We do realize, however, that change is not always easy for employees and for management in any company and implementing new processes or procedures and implementing new systems is difficult and time consuming. However, change is also inevitable. The business world is constantly evolving and companies should always be ready to adapt in a moment’s notice. So, before getting overwhelmed by the costs involved or the time and effort involved in this finding solutions to current inefficiencies at your business and implementing those solutions, think about the benefits and cost and time savings in the future.
What are your next steps?
Once management understands or realizes their main challenges and problems, it’s now time to gather all your key employees, from each department and write down their processes and day-to-day tasks. This not only allows management to fully understand what their teams are doing and how they are doing it, but also to help properly document important processes.
Next, it’s a great idea to share this documentation with the whole management team, business consultants, IT consultants and top department heads and determine if teams are working with the best and most efficient processes. If not, now is the time to go through each process and find solutions to challenges and better ways of doing things. In many cases, simply by implementing one system for all departments, like a complete ERP solution, with specific rights and permissions can solve a whole lot of headaches and improve efficiency right from the get-go.
In this case, with ONE software system, using ONE database, all employees will have access to important, accurate information. No need to go through hundreds of emails per day or find the latest Excel spreadsheets to find information related to products, sales, etc. This saves a lot of time, effort and critical mistakes!
So, if you are looking to increase data accessibility and visibility, reduce errors, increase efficiency and improve communication company-wide, contact our consultants today!
CONTACT US
400 Blvd Curé-Labelle, #304 Laval QC H7V 2S7 Canada
Phone: +1 450-681-3009
Email: support@namtek.ca
Website: https://www.namtek.ca/
Latest Blog Posts
 EDI Services in Canada: A Local Expert with 25+ Years of Integration ExperienceJanuary 30, 2026 - 8:53 pm
EDI Services in Canada: A Local Expert with 25+ Years of Integration ExperienceJanuary 30, 2026 - 8:53 pm How to Protect Your Business with Three Essential Levels of CybersecurityNovember 7, 2025 - 8:13 pm
How to Protect Your Business with Three Essential Levels of CybersecurityNovember 7, 2025 - 8:13 pm Managed Security Services (MSS) Explained: What They Are and Why Businesses Need ThemOctober 7, 2025 - 3:36 pm
Managed Security Services (MSS) Explained: What They Are and Why Businesses Need ThemOctober 7, 2025 - 3:36 pm
NEWSLETTER
Subscribe today to our Newsletter in order to stay up-to-date with all company news and events.




