Ransomware: Why You Should Care
Viruses extortionists (ransomware, cryptoviruses) work in a similar way: they block the user’s desktop, encrypt important documents and files saved on the computer, then delete the originals and demand a ransom. Typically in Bitcoin, so they can provide you with a key to unlock your computer and to be able to continue working and have access to your saved files. Often the creators of cryptoviruses have strict conditions for the terms of payment of the redemption. If the owner of the files does not fit within these terms, the key is deleted and it will be impossible for the user to restore the files.
Ransomware is the most massive and significant attacks of computer viruses in the world.
Here a chronology of the first viruses in history, as well as the largest-scale virus computer attacks.
In 1971, the first program in the world, which was able to independently reproduce copies of itself on a computer network, was created by the engineer of the American technology company BBN Technologies, Bob Thomas. The program, called Creeper was not malicious: its functionality was limited to self-copying and displaying the message: “I’m the creeper, catch me if you can!” A year later another BBN engineer, e-mail inventor Ray Tomlinson, created the first anti-virus that self-replicated on the network computers and deleted Creeper.
The first virus created in 1981 caused an uncontrolled “epidemic.” This virus spread using a technique now known as a boot sector virus. A virus called Elk Cloner was created by a 15-year-old American high school student Richard Skrenta by infecting the Apple II operating system. The virus infected the magnetic diskettes and, after the 50th access to the infected media a blank screen appears and a joke poem message was displayed. In some cases, the virus could also damage the floppy disk.
The first malicious program Michelangelo that infected over 1 million computers worldwide appeared in 1991 in Australia was written for IBM-compatible personal computers (PCs) and the DOS operating system. Other information from the disk could be restored, but it was difficult for an ordinary PC user to do it. The creator of the virus remained unknown, some cases of program activation were recorded until 1997.
On June 2, 1997, Chen Ing-hau, a student at the University of Datong (Taipei, Taiwan), created the first version of the Chernobyl virus (“Chernobyl” or CIH – according to the first syllables of the author’s name). The virus infected computers with operating systems Windows 95 and 98, triggers on April 26 of each year, the anniversary of the Chernobyl nuclear disaster. The virus erased the boot sector of the hard disk and, sometimes, the BIOS data – the boot sector of the computer. In the latter case, it was required to change the chip on the motherboard or even acquire a new computer, since the old one was out of order.
It is estimated that more than 60 million PCs were infected worldwide, and the damage exceeded $ 1 billion.
On May 5, 2000, the world’s largest epidemic of computer virus began. Created by Filipino students Reonel Ramones and Onel De Guzman, the “worm” ILOVEYOU sent itself to all e-mail contacts of the owner of the infected PC and replaced most of the files with documents, images and music on copies of itself. Only in the first 10 days of the epidemic, the number of infected computers exceeded 50 million. To protect themselves from the epidemic, many government agencies around the world have temporarily disconnected e-mail. The total damage was subsequently estimated at $ 15 billion. The Philippine police quickly found the creators of the virus. However, they went unpunished due to the lack of an article in the local criminal code providing responsibility for computer crimes.
On September 2010, the Stuxnet virus hit the computers of employees of the nuclear power station in Bushehr (Iran). It created problems in the functioning of centrifuges of the Uranium Enrichment Complex in Natanz. According to experts, Stuxnet was the first virus to be used as a cyber weapon.

On May 12, 2017 a significant number of computers with Windows as operating system were attacked by a virus-extortionist WannaCry. The virus encrypts user files so that they cannot be used. For decrypting the data, the attackers demanded $ 600 in the crypto currency of bitcoin.
According to Europol, the attack affected more than 200,000 computers across 150 countries. The four most affected countries were Russia, Ukraine, India and Taiwan according to Kaspersky Lab. The attack, in particular, affected the National Health Service hospitals of Great Britain. Up to 70,000 devices including computers, MRI scanners, blood-storage refrigerators, and theater equipment have been affected. Cyber risk modeling firm Cyence estimates the potential costs from the hack at $4 billion.
Don’t Miss: The Dangers of Ransomware & How To Overcome A Cyber Attack
On June 27, 2017, from the attack of a new variant of Petya Ransomware many of large organizations have suffered in multiple countries, but especially in Ukraine and Russia.
The Petya virus spreads through links in e-mail messages and blocks the user’s access to the computer hard drive, demanding a ransom of $ 300 in bitcoins. This is similar to the malicious program WannaCry. During this attack, the radiation monitoring system at Ukraine’s Chernobyl Nuclear Power Plant went offline. Some Ukrainian ministries, banks and metro systems were also affected. It is said to be the most destructive cyberattack ever.
The Business Continuity Solution to Ransomware
The best solution to protect your data and company from a different type of cyberattack is QBR (Quick Backup Recovery) Business Continuity Service, powered by Datto and provided by Namtek Consulting Services. QBR entails on-site real-time data and machine backup through virtualization as well as off-site backup to the cloud. This hybrid solution allows for quick recovery during a disaster with no downtime or data loss. For more information about the latest solutions in Backup and Recovery visit us at: Quick-Backup-Recovery.com



 This message is one that no business owner wants to see pop up on their office computer screen. Ransomware – a nasty and costly virus (or malware) that locks down computers and encrypts data until money (or a ransom) is sent – is not going anywhere. In fact, it seems to be such an epidemic these days as there are new malwares popping up and more victims paying up, which includes individuals, small and large organizations, hospitals, universities, government agencies and more.
This message is one that no business owner wants to see pop up on their office computer screen. Ransomware – a nasty and costly virus (or malware) that locks down computers and encrypts data until money (or a ransom) is sent – is not going anywhere. In fact, it seems to be such an epidemic these days as there are new malwares popping up and more victims paying up, which includes individuals, small and large organizations, hospitals, universities, government agencies and more.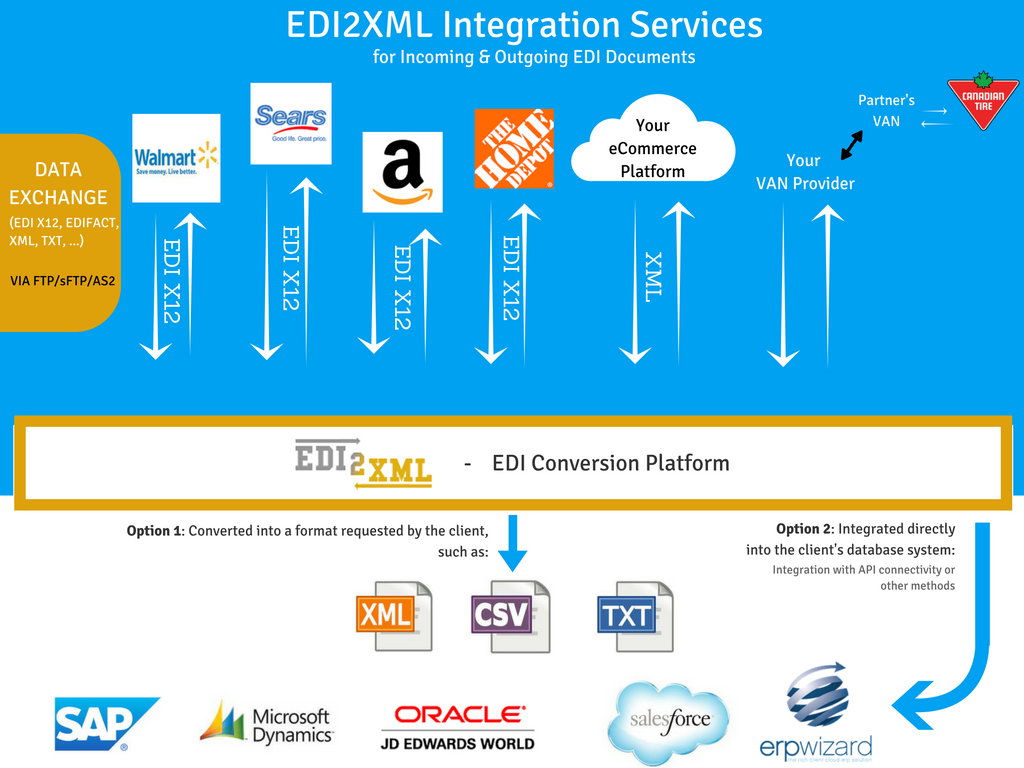
 We are certain that demand for these management solutions will only increase, as executives are actively looking to transform their businesses using the latest technologies on the market. We predict that mobile business applications will make this list next year, as business owners are looking to supply their on-site teams with access to their management system to input and review real-time data. Modern, visually appealing, easy to use applications don’t just have to be for personal use; companies should be benefiting from these types of applications as well! One thing is for certain; businesses are looking beyond the brand name when it comes to software systems and taking the time to ensure that the Software Provider and offerings are a good fit for their company.
We are certain that demand for these management solutions will only increase, as executives are actively looking to transform their businesses using the latest technologies on the market. We predict that mobile business applications will make this list next year, as business owners are looking to supply their on-site teams with access to their management system to input and review real-time data. Modern, visually appealing, easy to use applications don’t just have to be for personal use; companies should be benefiting from these types of applications as well! One thing is for certain; businesses are looking beyond the brand name when it comes to software systems and taking the time to ensure that the Software Provider and offerings are a good fit for their company. What is “data insurance”? To our team at Namtek Consulting Services, it is a company’s Business Continuity and Disaster Recovery solution and plan. All of our customers, using our QBR Business Continuity solution and service refer to their monthly fee as their data’s insurance policy. They know that no matter what happens, their data is protected and easily recoverable. They are provided with real-time backups, email confirmations ensuring that all backups taken were successful, and quick recovery methods for their data during any crisis or disaster. Please don’t get this mixed up with those old backup tapes and drives.
What is “data insurance”? To our team at Namtek Consulting Services, it is a company’s Business Continuity and Disaster Recovery solution and plan. All of our customers, using our QBR Business Continuity solution and service refer to their monthly fee as their data’s insurance policy. They know that no matter what happens, their data is protected and easily recoverable. They are provided with real-time backups, email confirmations ensuring that all backups taken were successful, and quick recovery methods for their data during any crisis or disaster. Please don’t get this mixed up with those old backup tapes and drives.  In the end, what matters to every business owner, is how fast employees can get back to work or in other words, how quickly operations can resume, during all sorts of disasters or crises. Be it a fire, a flood, an ice storm (for all our fellow Canadians), a human error, a ransomware attack, or hardware malfunction, it’s important to be well protected. A company’s data is extremely valuable to their operations and it’s time business owners see Business Continuity services as their insurance policy. Our QBR customers can restore an entire server, an entire desktop or simply pick and choose a specific file they accidentally deleted. It’s that simple and truly that remarkable.
In the end, what matters to every business owner, is how fast employees can get back to work or in other words, how quickly operations can resume, during all sorts of disasters or crises. Be it a fire, a flood, an ice storm (for all our fellow Canadians), a human error, a ransomware attack, or hardware malfunction, it’s important to be well protected. A company’s data is extremely valuable to their operations and it’s time business owners see Business Continuity services as their insurance policy. Our QBR customers can restore an entire server, an entire desktop or simply pick and choose a specific file they accidentally deleted. It’s that simple and truly that remarkable.